Malware often uses exploits to infect devices and spread. The Windows 10 Exploit Protection feature provides malware security by applying process-limiting techniques to the operating system and individual applications. If you are certain of the applications you are using and want to add an application as an exception to Protection against exploits Windows Defender in Windows 10, follow the instructions in the message.
Add or exclude an app in protection against exploits
Reports were reported by users whose gaming performance was lower than the activation of the feature. Windows notes that some of the security mitigation technologies may have compatibility issues with certain applications. As such, you can disable protection for such applications.
To disable exploit protection for some applications in Windows 10:
- Open Settings
- Click on Update and security
- Move towards Windows security
- To select Control of the application and the browser
- Scroll to find Protection settings against exploits link
- Click on it.
Now you need to add an exception to the protection against exploits settings
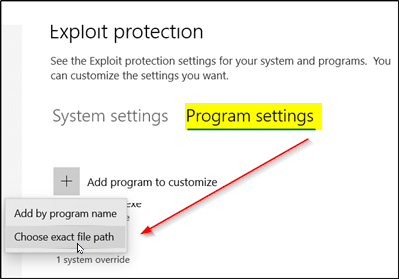
Switch to & #39;Program settings'Tab. The tab allows you to choose the application to which you want to apply mitigation measures.
If the application you want to configure is not in the list, choose "Add a program to customize » then choose how you want to add the application.
You will have two options-
- Add by program name – allows you to apply mitigation measures to any ongoing process with that name. However, you must specify the file with its extension. In addition, you can enter a full path to limit the mitigation to only the application with that name at that location.
- Choose the exact path of the file – uses a file selection window in standard Windows Explorer to search for and select the desired file.
In this case, we use a standard Windows Explorer file selection window, which is the second option to access the file for which we want to add an exception.
Once found and selected, a long list of parameters will open. You will see here a list of all the mitigation measures that can be applied. For example, by choosing "Verification & #39; will apply attenuation in audit mode only.
To completely exclude the application of Exploit Mitigation, uncheck the corresponding boxes.
Repeat the procedure for all applications that you want to exclude from Exploit Mitigation.
Click & #39;Apply'When you have finished configuring your configuration.
The changes made will require the restart of the file.
So, close and quit and restart the file. Please also note that you will need administrator rights to make the desired changes.
I hope you find the instructions easy to understand.