Thunderclap is the hardware brand interface developed by Intel. It acts as an interface between the computer and external devices. While most Windows computers come with all kinds of ports, many companies use Thunderbolt to connect to different types of devices. It facilitates connection, but according to research at Eindhoven University of Technology, the security behind Thunderbolt can be breached using a technique – Thunderspy. In this article, we will share tips that you can follow to protect your computer from Thunderspy.
What is Tunderspy? How it works?
It is a stealth attack which allows an attacker to access the Direct Memory Access (DMA) functionality to compromise devices. The biggest problem is that no trace remains as it works without deploying the spirit of malware or link bait. It can bypass security best practices and lock the computer. So how does it work? The attacker needs direct access to the computer. According to research, it takes less than 5 minutes with the right tools.
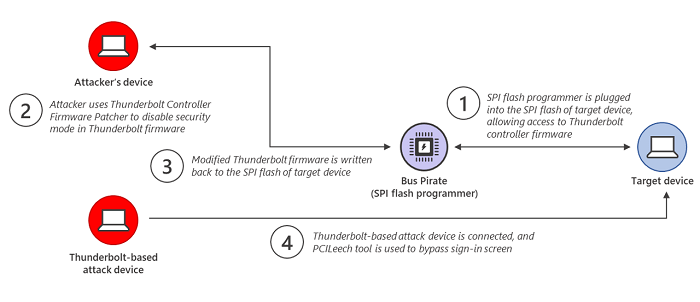
The attacker copies the Thunderbolt controller firmware from the source device to his device. It then uses a firmware corrector (TCFP) to deactivate the security mode applied in the Thunderbolt firmware. The modified version is copied to the target computer using the Bus Pirate device. A Thunderbolt-based attack device is then connected to the attacked device. It then uses the PCILeech tool to load a kernel module that bypasses the Windows login screen.
So even if the computer has security features like secure boot, solid BIOS and operating system account passwords and full disk encryption enabled, it will bypass everything.
POINT: Spycheck goes check if your PC is vulnerable to Thunderspy attack.
Tips to protect yourself from Thunderspy
Microsoft recommended three ways to protect yourself from the modern threat. Some of these features built into Windows can be exploited while others must be activated to mitigate attacks.
- PC protection with secure core
- DMA kernel protection
- Integrity of code protected by hypervisor (HVCI)
That said, all this is possible on a PC with a secure core. You simply cannot apply this on a normal PC as the hardware is not available to protect it from attack. The best way to find out if your PC supports it is to consult the Devic Security section of the Windows Security application.
1]PC protection with secure core
Windows Security, Microsoft’s internal security software, provides Windows Defender System Guard and virtualization-based security. However, you need a device that uses secure core PCs. It uses hardware security rooted in the modern processor to launch the system into a state of trust. It helps mitigate malware attempts at the firmware level.
2]DMA kernel protection
Introduced in Windows 10 v1803, DMA kernel protection ensures that external devices are blocked from DMA (Direct Memory Access) attacks using PCI hotplug devices such as Thunderbolt. This means that if someone tries to copy the malicious Thunderbolt firmware to a machine, they will be blocked on the Thunderbolt port. However, if the user has the username and password, they can bypass it.
3]Reinforced protection with code integrity protected by hypervisor (HVCI)
The integrity of code protected by the hypervisor or HVCI must be activated on Windows 10. It isolates the code integrity subsystem and verifies that the kernel code is not verified and signed by Microsoft. It also ensures that the kernel code cannot be both writable and executable to ensure that the unverified code does not run.
Thunderspy uses the PCILeech tool to load a kernel module that bypasses the Windows login screen. Using HVCI will take care to avoid this as it will not allow it to execute the code.
Security should always be at the top when it comes to buying computers. If you are processing important data, especially for businesses, it is recommended to buy secure core PC devices. Here is the official page of these devices on the Microsoft website.