What is WDAGUtilityAccount in Windows 10? Should I delete it?

If you open the command prompt and run the command surfer on your Windows 10 system you can see a WDAGUtilityAccount Entrance. What is it? Is it a malware? What exact role does it play and is it prudent to remove it? Let us find answers to these questions in today's post.
WDAGUtilityAccount in Windows 10
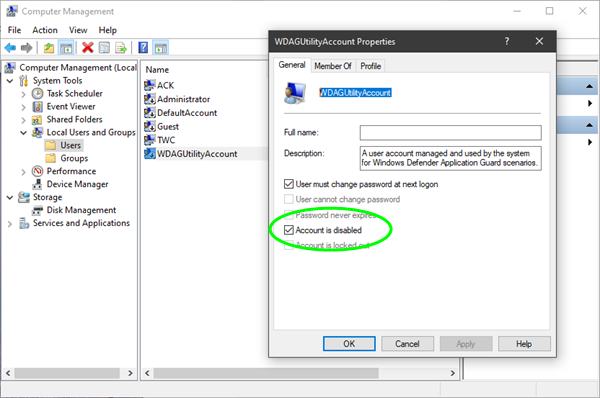
WDAGUtilityAccount is a user account that is managed and used by the system for Windows Defender Application Guard scenarios.
WDAGUtilityAccount is part of Windows Defender Application Guard. It remains off until Application Guard is enabled on your system. There are several system accounts built into Windows and WDAGUtilityAccount is one.
When this option is enabled, your logging solution may display an alert for a new local account created for the user name: WDAGUtilityAccount (Event ID 4720 or 4722). This can sometimes annoy you – for example, when you try to delete a file, you are prompted to Access is denied, the authorization of the administrator is required message. When you choose to ignore it and press 'Continue', you receive another message telling you that you need authorization from another account – WDAGUtilityAccount. But this is for your safety.
You can check if WDAGUtilityAccount is active on your system as follows:
- Open the WinX menu
- Select Computer Management
- Develop system tools
- Expand Local Users and Groups
- Double click on the Users folder and you will see it!
Double-clicking it will open its properties. Here you will see whether it is active or not.
Can you delete or rename the WDAGUtility account?
As the WDAGUtility account is a special "system managed account" in Windows 10, it is not recommended to rename or delete it using the Administrator account.
I hope it helps.